The syntax for running an xprobe2 fingerprint is really straightforward. Later some good results with the same command; Weird. It also shows us that espn. I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. A much better fingerprinting method is to look at DHCP packets since they reveal a lot about the host. 
| Uploader: | Mele |
| Date Added: | 24 August 2004 |
| File Size: | 39.11 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 21291 |
| Price: | Free* [*Free Regsitration Required] |
It also shows us that espn.
Xprobe2 download, free Xprobe2 download.
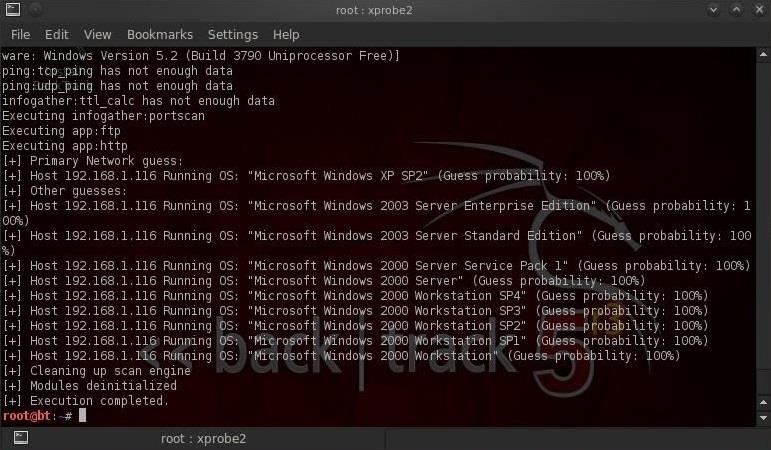
As I mentioned earlier, xprobe2 has 16 modules that it uses to try to determine the operating system of the target. The only things about active OS fingerprinting is that it can be done foe any network as long as the fingerprinted host is reachable. It depends upon what you mean by obsolete.
The tester should be comfortable with all the tools he decide to use, they are never a replacement for good understanding of x. Xprobe2 then identifies, with lower probability of being correct, the Linux kernel version of the server. It just messes up badly on larger networks.
Among the information we need to gather are the open ports, wibdows services, and the operating system.
It uses each of them to try to determine the probability of its guess. In the case of xprobe2, you can simply update the signatures for newer OS's and everything works. When you use xprobe2, does your IP get logged into the computer you are sending packets to? Option should be used in conjunction with - T. Possible values for proto are tcp or udp, portnum can only take values from 1 tostate can be either closed for tcp that means that remote host replies with RST packet, for udp that means that remote host replies with ICMP Port Unreachable packet or open for tcp that means that remote host replies with SYN ACK packet and for udp that means that remote host doesn' t send any packet back.
Hi, How were you able to resolve the bug of unreadable text for the guessed OS names? And I still fail to see how I did! How were you able to resolve the bug of unreadable text for the guessed OS names?
Let xprobe2 stay the way it is, and try and slim nmap down a bit. During analysis module will search for different packets, based on some of the fields of TCP and IP headers, withing the same class and if such packets are found, message will be displayed showing different packets withing the same class.
Because i think mine is really outdated lol. To find it, type:. For that reason I prefer unicornscan over nmap.
Xprobe2 Download – Active OS Fingerprinting Tool
xproe2 Xprobe2, like nmap and hping, is an essential reconnaissance tool that should be in every hacker's toolbox. Yes Unicorn does TCP as well and it does it better for large networks but I still find nmap better for TCP investigation and trickery idle scans, decoys, banner grabbing etc.
Sifmole January 9, at 5: How to Hack Wi-Fi: Apart from that I really prefer doing passive OS fingerprinting.

Do any of you know where you can find updated databases? What they should do with nmap is improve their UDP-scanning.
Xprobe2 Download – Active OS Fingerprinting Tool - Darknet
In this tutorial, we'll use one of the best active tools for doing OS fingerprinting, xprobe2which is an active OS fingerprinter, meaning that it actually sends probes to the target system, then gauges the OS from the system's response. Words are not enough to describe this tool. Although such tools as nmap and hping2 can do operating system fingerprinting, they are not as accurate and reliable as the tools that are built specifically for this purpose.
The syntax for running an xprobe2 fingerprint is really straightforward. Would be nice to see all of these features combined with nmap. Sounds like a very useful tool. Later some good results with the same command; Weird xprobe2 -L responds with the help page, not the list of modules.

No comments:
Post a Comment